In an age where cyber threats are growing more sophisticated, the need for robust security systems has never been more critical. One of the most effective ways to safeguard online accounts and sensitive data is through Multi-Factor Authentication (MFA). As we move into 2025, the importance of MFA has only increased. In this blog post, we’ll explore why MFA is essential in today’s digital landscape, how it works, and why it will remain a cornerstone of cybersecurity.
What is Multi-Factor Authentication (MFA)?
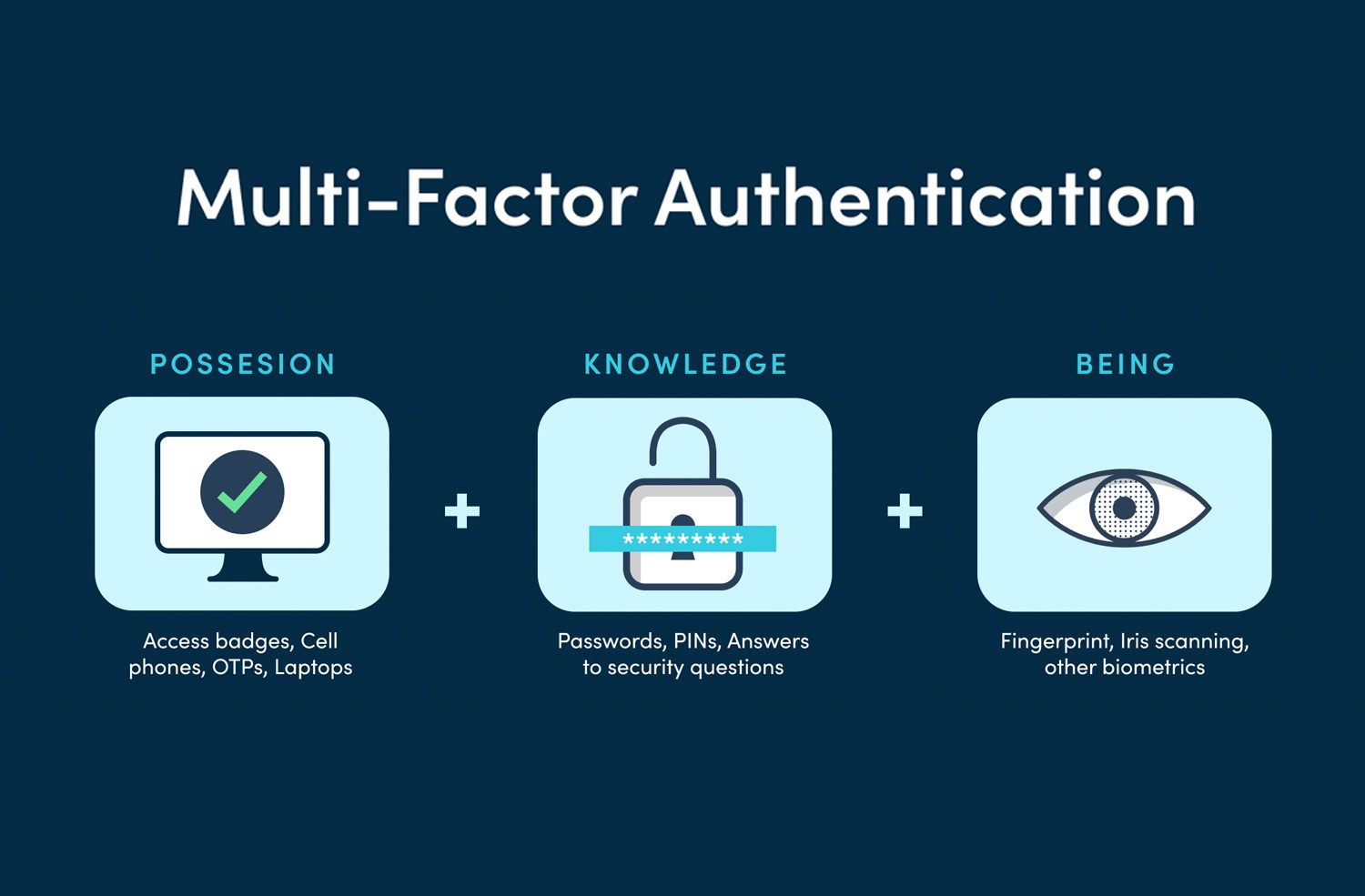
Multi-Factor Authentication is a security process that requires users to provide two or more forms of identity verification before granting access to a system, account, or resource. Unlike traditional single-factor authentication, which typically relies on just a password, MFA combines multiple layers of security. These layers generally fall into three categories:
- Something you know: A password, PIN, or passphrase.
- Something you have: A physical device such as a smartphone, hardware token, or a smart card.
- Something you are: Biometrics, such as fingerprints, facial recognition, or voice recognition.
This approach makes it significantly more difficult for cybercriminals to gain unauthorized access, even if they have compromised one factor, such as a password.
The Growing Cybersecurity Threats in 2025
As we approach 2025, the cybersecurity landscape continues to evolve, and so do the threats. Cybercriminals have become increasingly adept at exploiting weaknesses in systems, often using advanced techniques such as phishing, credential stuffing, and man-in-the-middle attacks to bypass traditional security measures. Passwords alone no longer provide adequate protection.
Some key statistics highlight the seriousness of the situation:
- According to recent data, over 80% of data breaches involve weak or stolen passwords.
- In 2024 alone, ransomware attacks increased by nearly 40%, with many hackers leveraging stolen credentials as a primary entry point.
These trends demonstrate the urgent need for stronger authentication mechanisms. While passwords are still widely used, they are also one of the weakest links in cybersecurity. A user might use weak passwords, reuse them across different platforms, or fall victim to phishing attempts—all of which make them easy targets for hackers.
Why MFA is Essential in 2025
With cyber threats becoming more sophisticated, MFA offers several advantages over traditional password-only authentication:
1. Increased Protection Against Credential Theft
One of the main reasons for implementing MFA is that it significantly reduces the risk of unauthorized access due to stolen credentials. If an attacker obtains a user’s password through a breach or phishing attack, they would still need to bypass the second factor of authentication. This might be a one-time code sent to the user’s phone, a biometric scan, or a hardware token—making it much harder for cybercriminals to succeed.
2. Protecting Sensitive Data and Resources
As businesses and individuals continue to store sensitive information online—whether it’s financial data, healthcare records, or intellectual property—ensuring that only authorized users can access this information is paramount. MFA helps to secure everything from corporate systems to personal accounts, reducing the risk of sensitive data being exposed in the event of a breach.
3. Minimizing Human Error
Even the most vigilant users can make mistakes. Whether it’s clicking on a malicious link in an email or using the same password across multiple sites, human error is often to blame for cybersecurity incidents. MFA provides an additional layer of security that compensates for these mistakes. Even if a user inadvertently exposes their password, the second factor can act as a barrier against unauthorized access.
4. Compliance with Increasing Regulations
As cybersecurity concerns grow, many industries are facing stricter regulations regarding data security and privacy. For example, the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) have increased pressure on organizations to protect sensitive information. In 2025, we can expect even more industries to adopt regulations requiring multi-factor authentication, especially for services involving critical data.
5. Improved Customer Trust
For businesses, implementing MFA shows a proactive commitment to securing customer data and prioritizing their privacy. In an era where breaches and hacks make headlines, consumers are more aware of the importance of their online security. Providing them with MFA options helps build trust, showing that you’re serious about safeguarding their personal information.
Common MFA Methods and Their Effectiveness
While there are various ways to implement MFA, it’s essential to choose methods that provide both security and user convenience. Here are a few common methods:
- SMS-based Authentication
- How it works: A one-time code is sent via SMS to the user’s phone.
- Pros: Easy to implement and use.
- Cons: Vulnerable to SIM-swapping attacks and phishing.
- How it works: A one-time code is sent via SMS to the user’s phone.
- Authenticator Apps (e.g., Google Authenticator, Authy)
- How it works: An app generates time-based one-time passwords (TOTPs) that are used to authenticate the user.
- Pros: More secure than SMS, as the codes are generated locally on the device.
- Cons: Users need to install and configure the app.
- How it works: An app generates time-based one-time passwords (TOTPs) that are used to authenticate the user.
- Hardware Tokens (e.g., YubiKey)
- How it works: A physical device is used to generate or store authentication data.
- Pros: Very secure; physical device needed for authentication.
- Cons: Can be lost or stolen, though it’s much harder for an attacker to use without physical possession.
- How it works: A physical device is used to generate or store authentication data.
- Biometric Authentication
- How it works: Uses a user’s biometric data (e.g., fingerprints, facial recognition) for authentication.
- Pros: Extremely user-friendly and highly secure.
- Cons: May have privacy concerns, and the technology may not be available for all devices.
- How it works: Uses a user’s biometric data (e.g., fingerprints, facial recognition) for authentication.
The Future of MFA in 2025 and Beyond
As cyber threats continue to evolve, so too will multi-factor authentication. By 2025, we can expect several advancements and trends to emerge in MFA:
- Passwordless Authentication: With the development of technologies like WebAuthn and FIDO2, passwordless authentication will become more mainstream. Users will rely on biometrics, smartcards, or mobile devices to authenticate without ever needing a password.
- Contextual MFA: Instead of asking for multiple authentication factors every time, contextual MFA will assess factors like the user’s location, device, and behavior patterns to decide when to prompt for additional verification.
- AI-Powered Authentication: Artificial intelligence (AI) will be used to improve the security of MFA systems by analyzing behavior patterns and detecting anomalies in real-time.
Conclusion
As we move into 2025, the role of Multi-Factor Authentication in cybersecurity will only become more critical. Passwords alone are no longer sufficient to protect sensitive data and resources. By implementing MFA, organizations and individuals can significantly reduce the risk of unauthorized access and safeguard themselves from the growing wave of cyber threats. Whether you’re a business leader or an individual user, adopting MFA is one of the simplest yet most effective ways to bolster your security in the digital age.